There is a known bug in the Certificate Enrollment Policy Web Service (CEP) that causes certificate templates configured for compatibility with Windows Server 2016 or Windows 10 not to display.
The Certificate Enrollment Web Services (Certificate Enrollment Policy Web Service, CEP, and Certificate Enrollment Web Service, CES) enable the automatic request and renewal of certificates from a certification authority via a Web-based interface. This eliminates the need to contact the certification authority directly via Remote Procedure Call (RPC). For a more detailed description, see the article "Certificate request basics via Certificate Enrollment Web Services (CEP, CES)„.
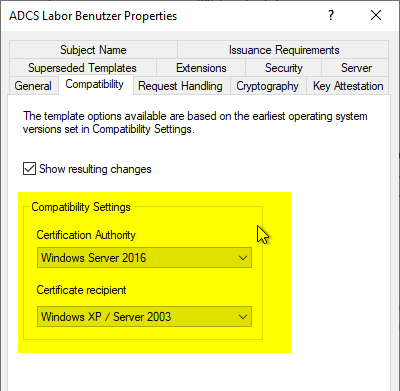
It is irrelevant here whether compatibility is set only for the certification authority or for certificate recipients on Windows Server 2016 or Windows 10. In both cases, the certificate template is not displayed by the CEP.
Apparently, the certificate template is filtered out if any of the following cases apply:
- The CTPRIVATEKEY_FLAG_SERVERVERSION_SHIFT flag in the msPKI private key flag attribute of the certificate template is configured to TEMPLATE_SERVER_VER_THRESHOLD.
- The CTPRIVATEKEY_FLAG_CLIENTVERSION_SHIFT flag in the msPKI private key flag attribute of the certificate template is configured to TEMPLATE_CLIENT_VER_THRESHOLD.
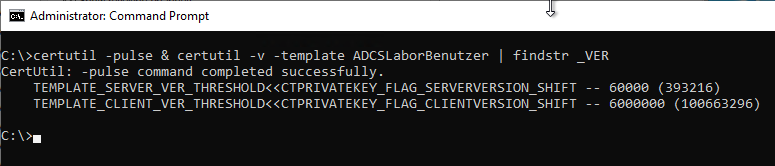
For more details on this, see article "How are the compatibility settings for certificate templates technically mapped?„.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Among other things, this leads to the following phenomenon:
- If the request for a certificate is made via Windows Powershell (Get-Certificate), the request fails. See also article "Requesting certificates via Certificate Enrollment Web Services using Windows PowerShell fails with error message "Cannot find object or property. 0x80092004 (-2146885628 CRYPT_E_NOT_FOUND)"„
- If the request for a certificate is made through the Microsoft Management Console (MMC), the certificate template is not displayed or the list of certificate templates is empty. See the article "Requesting a certificate fails with the error message "You cannot request a certificate at this time because no certificate types are available."„
Since Microsoft has published a knowledge base article about this problem, but no hotfix so far, it can be assumed that the bug will not be fixed.
So the only thing left to do is to configure the certificate template compatibility to Windows Server 2012 R2 or smaller, if possible.
6 thoughts on “Der Zertifikatregistrierungs-Richtliniendienst zeigt Zertifikatvorlagen, die auf Kompatibilität mit Windows Server 2016 oder Windows 10 konfiguriert sind, nicht an”
Comments are closed.