The following is an overview of the audit events generated by the certification authority in the Windows Event Viewer.
In contrast to operational events, which are often understood under the term "monitoring", auditing for the certification authority is the configuration of logging of security-relevant events.
Event Sources
Audit events are always written to the security log. They always come from the Microsoft Windows Security Auditing source. The events relevant for the certification authority have the ID numbers 4868 to 4900.
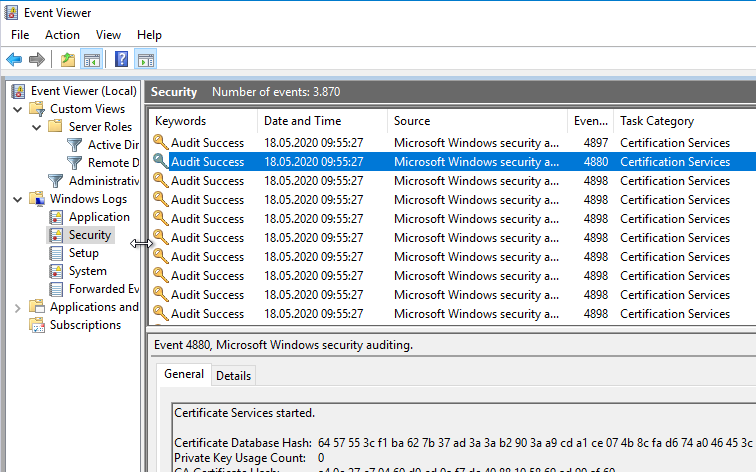
Activate auditing
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
Audit events are not written until the certification authorities have been configured to do so. For a description of the procedure, see the article "Configuration of security event monitoring (auditing settings) for certification authorities„.
Enable extended audit events
Events 4898 to 4900 are generated only when a corresponding configuration setting (the flag EDITF_AUDITCERTTEMPLATELOAD) was set on the certification authority.
certutil -setreg policy\EditFlags +EDITF_AUDITCERTTEMPLATELOAD
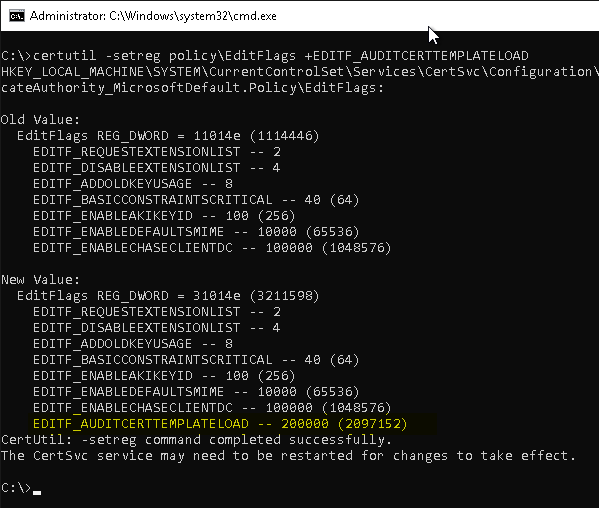
Subsequently, a restart of the Certification Authority service is required to apply the settings.
Events
| ID | Event text |
|---|---|
| 4868 | The certificate manager denied a pending certificate request. Request ID: %1 |
| 4869 | Certificate Services received a resubmitted certificate request. Request ID: %1 |
| 4870 | Certificate Services revoked a certificate. Serial Number: %1 Reason: %2 |
| 4871 | Certificate Services received a request to publish the certificate revocation list (CRL). Next Update: %1 Publish Base: %2 Publish Delta: %3 |
| 4872 | Certificate Services published the certificate revocation list (CRL). Base CRL: %1 CRL Number: %2 Key Container: %3 Next Publish: %4 Publish URLs: %5 |
| 4873 | A certificate request extension changed. Request ID: %1 Name: %2 Type: %3 Flags: %4 Data: %5 |
| 4874 | One or more certificate request attributes changed. Request ID: %1 Attributes: %2 |
| 4875 | Certificate Services received a request to shut down. |
| 4876 | Certificate Services backup started. Backup Type: %1 |
| 4877 | Certificate Services backup completed. |
| 4878 | Certificate Services restore started. |
| 4879 | Certificate Services restore completed. |
| 4880 | Certificate Services started. Certificate Database Hash: %1 Private Key Usage Count: %2 CA Certificate Hash: %3 CA Public Key Hash: %4 |
| 4881 | Certificate Services stopped. Certificate Database Hash: %1 Private Key Usage Count: %2 CA Certificate Hash: %3 CA Public Key Hash: %4 |
| 4882 | The security permissions for Certificate Services changed. %1 |
| 4883 | Certificate Services retrieved an archived key. Request ID: %1 |
| 4884 | Certificate Services imported a certificate into its database. Certificate: %1 Request ID: %2 |
| 4885 | The audit filter for Certificate Services changed. Filter: %1 |
| 4886 | Certificate Services received a certificate request. Request ID: %1 Requester: %2 Attributes: %3 |
| 4887 | Certificate Services approved a certificate request and issued a certificate. Request ID: %1 Requester: %2 Attributes: %3 Disposition: %4 SKI: %5 Subject: %6 |
| 4888 | Certificate Services denied a certificate request. Request ID: %1 Requester: %2 Attributes: %3 Disposition: %4 SKI: %5 Subject: %6 |
| 4889 | Certificate Services set the status of a certificate request to pending. Request ID: %1 Requester: %2 Attributes: %3 Disposition: %4 SKI: %5 Subject: %6 |
| 4890 | The certificate manager settings for Certificate Services changed. Enable: %1 %2 |
| 4891 | A configuration entry changed in Certificate Services. Node: %1 Entry: %2 Value: %3 |
| 4892 | A property of Certificate Services changed. Property: %1 Index: %2 Type: %3 Value: %4 |
| 4893 | Certificate Services archived a key. Request ID: %1 Requester: %2 KRA Hashes: %3 |
| 4894 | Certificate Services imported and archived a key. Request ID: %1 |
| 4895 | Certificate Services published the CA certificate to Active Directory Domain Services. Certificate Hash: %1 Valid From: %2 Valid To: %3 |
| 4896 | One or more rows have been deleted from the certificate database. Table ID: %1 Filter: %2 Rows Deleted: %3 |
| 4897 | Role separation enabled: %1 |
| 4898 | Certificate Services loaded a template. %1 v%2 (Schema V%3) %4 %5 Template Information: Template Content: %7 Security Descriptor: %8 Additional Information: Domain Controller: %6 |
| 4899 | A Certificate Services template was updated. %1 v%2 (Schema V%3) %4 %5 Template Change Information: Old Template Content: %8 New Template Content: %7 Additional Information: Domain Controller: %6 |
| 4900 | Certificate Services template security was updated. %1 v%2 (Schema V%3) %4 %5 Template Change Information: Old Template Content: %9 New Template Content: %7 Old Security Descriptor: New Security Descriptor: %8 Additional Information: Domain Controller: %6 |
If the certification authority uses software keys, these events are also interesting:
| ID | Event text |
|---|---|
| 5058 | Key file operation. Subject: Security ID: %1 Account Name: %2 Account Domain: %3 Logon ID: %4 Cryptographic Parameters: Provider Name: %5 Algorithm Name: %6 Key Name: %7 Key Type: %8 Key File Operation Information: File Path: %9 Operation: Return Code: |
| 5059 | Key migration operation. Subject: Security ID: %1 Account Name: %2 Account Domain: %3 Logon ID: %4 Cryptographic Parameters: Provider Name: %5 Algorithm Name: %6 Key Name: %7 Key Type: %8 Additional Information: Operation: %9 Return Code: |
6 thoughts on “Übersicht über die von der Zertifizierungsstelle generierten Audit-Ereignisse”
Comments are closed.