Assume the following scenario:
- You try to apply for a certificate from an Active Directory-integrated certification authority (Enterprise Certification Authority).
- To do this, use the Microsoft Management Console (MMC), either for the logged-in user (certmgr.msc) or for the computer (certlm.msc).
- However, the desired certificate template is not displayed for selection, even though it has been correctly published on the certification authority.
- The logged-in user (or computer) also has the necessary permissions to request certificates from the certificate template in question (enroll).
- In the list of available certificate templates within the MMC, all certificate templates are displayed. At the desired certificate template is written:
A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.
A general overview block on the underlying functionality is provided by the articles "Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)" and "Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM„.
Causes
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
To be able to narrow down the error further, a closer look at the description text helps.
Error "The requested certificate template is not supported by this CA."
The German variant of the description reads "The requested certificate template is not supported by this certification authority (CA).".
Of course, this only applies if the required certificate template has actually been published on the certification authority.
The requested certificate template is not supported by this CA. A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.
This error indicates that the position of trust cannot be established with the issuing Certification Authority.
In this case, the following should be checked:
- Is the root CA stored in the corresponding repository for trusted root CAs?
- Are all intermediate CAs (if any) stored in the intermediate CA certificate store? (This store is automatically populated on domain clients from the "AIA" object of the Public Key Services container in Active Directory. Accordingly, it should be checked whether the certificates are also stored there).
Error "The permissions on this certification authority do not allow the current user to enroll for certificates" or "Cannot find object or property".
The permissions on this certification authority do not allow the current user to enroll for certificates. A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.
or
The German variant of the description is "Das Objekt oder die Eigenschaft wurde nicht gefunden".
Cannot find object or property. A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.
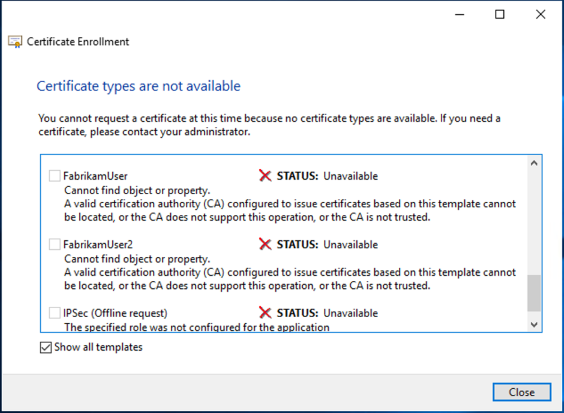
This error can occur, for example, if the logged-in user does not have rights to request certificates from the certification authority.
Root Cause Analysis
In addition to the authorization within the certificate template, there is also a right directly on the certification authority to be able to obtain certificates from it (request certificates).
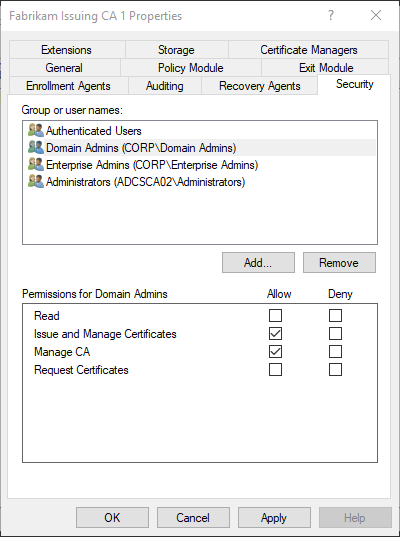
The corresponding dialog can be accessed in the management console of the certification authority (certsrv.msc) by right-clicking on the CA name, then "Properties", in the "Security" tab. By default, authenticated users have the right to request certificates.
In the present case, this right was also displayed accordingly in the security tab of the certification authority. Nevertheless, no certificates could be requested from the certification authority. As a test, the certificate template was published on another certification authority, where it could be requested.
The permissions set in the Security tab are saved in two places:
- In the registry database of the certification authority service under HKLM:\CurrentControlSet\Services\CertSvc\Configuration\{name-of-certification authority}\ in the value "Security".
- In the Access Control List (ACL) of the "Public Key Services" object in Active Directory in the pKIEnrollmentService object belonging to the certification authority below CN=Enrollment Services. If the security permissions have been changed by the certification authority's management console, the certification authority's computer account will update the Active Directory object accordingly.
The value within the registry can be viewed either through the certificate authority management console (certsrv.msc) or through the following command line command:
certutil -getreg CA\Security
Example:
certutil -getreg CA\Security
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\Fabrikam Issuing CA 1\Security:
Security REG_BINARY =
Allow Enroll NT AUTHORITY\Authenticated Users
Allow CA Administrator Certificate Manager CORP\Domain Admins
Allow CA Administrator Certificate Manager CORP\Enterprise Admins
Allow CA Administrator Certificate Manager BUILTIN\Administrators
CertUtil: -getreg command completed successfully.
The permissions on the Active Directory object can be displayed either via the ADSI editor (adsiedit.msc), or via the command line.
The ADSI Editor is only suitable for this task to a limited extent, since ADCS-specific permissions are not resolved in some cases. The command line variant is better suited:
certutil [options] -ds [CN]
For example, with the -v option, the CN (Common Name) of the corresponding pKIEnrollmentService object, and the nTSecurityDescriptor attribute, the command looks like this:
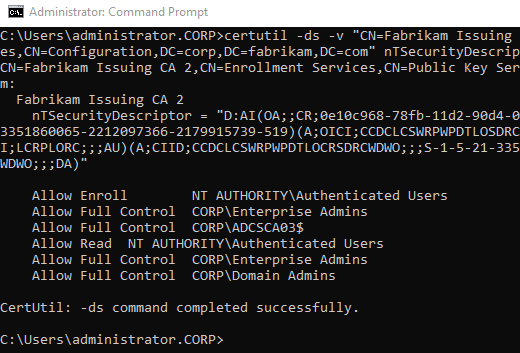
certutil -ds -v "CN={Common-Name-of-CA},CN=Enrollment Services,CN=Public Key Services,CN=Services,CN=Configuration,{Root-DN-of-total-structure}" nTSecurityDescriptor
In the case of the Certification Authority in question, this issue came to light:
Allow Full Control CORP\Enterprise Admins
Allow Full Control CORP\ADCSCA03$
Allow Read NT AUTHORITY\Authenticated Users
Allow Full Control CORP\Enterprise Admins
Allow Full Control CORP\Domain Admins
As you can see, the permission for the authenticated users to request certificates is missing here. Apparently, the registry and Active Directory are not in sync.
Cause
In the present case, the Certification Authority migrated to a new server. For this purpose, a backup of the certification authority was created and stored on a new server restored. To prevent certificates from being requested during the migration of the certification authority, the Authenticated User Principal was temporarily stripped of the rights to request certificates. However, this was done after the registration of the certification authority was backed up on the source server.
Thus, a registry was restored on the target server, apparently allowing Authenticated Users to request certificates, but the pKIEnrollmentService object in Active Directory was not correctly updated again.
Solution
The solution was to remove the authorization again locally on the certification authority and re-enter it. Afterwards, the pKIEnrollmentService object was again in sync with the certification authority:
Related links:
- Putting an Active Directory integrated certification authority (Enterprise Certification Authority) into maintenance mode
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
- Troubleshooting for automatic certificate request (autoenrollment) via RPC/DCOM
External sources
- certutil (Microsoft)
5 thoughts on “Die Beantragung eines Zertifikats schlägt fehl mit der Fehlermeldung „A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.“”
Comments are closed.