Delegation is required whenever there is an intermediary between the user and the actual service. In the case of certification authority web registration, this would be the case if it is installed on a separate server. It then acts as an intermediary between the applicant and the certification authority.
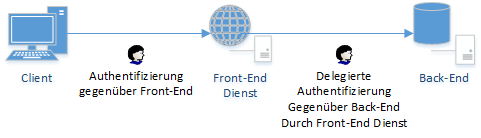
The applicant authenticates itself to the web service - which in turn must authenticate itself to the certification authority on behalf of the applicant.
Since this is a security-relevant function, accounts must be explicitly configured for delegation.
Overview of the different options
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The delegation settings can be set via the Active Directory Users and Computers management console (dsa.msc). However, to do this, the "Advanced Features" option must first be activated under "View".
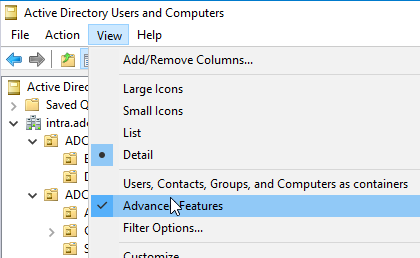
Looking at the Delegation tab for a user or computer account, the following options are available:
- Do not trust this user for delegation
- Trust this user for delegation to any service (Kerberos only)
- Trust this user for delegation to specified services only: Use Kerberos only
- Trust this user for delegation to specified services only: Use any authentication protocol
Details: Do not trust this user for delegation
If this option is selected, no delegation can be performed with the account. This would be the case if the web service were installed directly on the same server as the certification authority, but this is not recommended for security reasons: No web server should be installed on the certification authority, nor should any deprecated code be run on it, as in the case of the certification authority web registration.
Details: Trust this user for delegation to any service (Kerberos only)
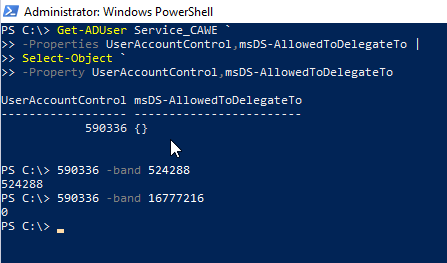
Technically, this setting is mapped by setting bit 524288 (TRUSTED_FOR_DELEGATION) in the UserAccountControl attribute of the service account.
If this option is selected, the account can perform delegated authentication to any existing service.
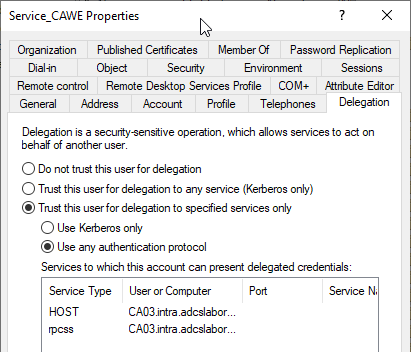
Details: Trust this user for delegation to specified services only: Use Kerberos only
Technically, this option is mapped by the fact that the target services are entered in the msDS-AllowedToDelegateTo attribute of the service account and neither bit 524288 (TRUSTED_FOR_DELEGATION), nor bit 16777216 (TRUSTED_TO_AUTH_FOR_DELEGATION) are set in the UserAccountControl attribute.
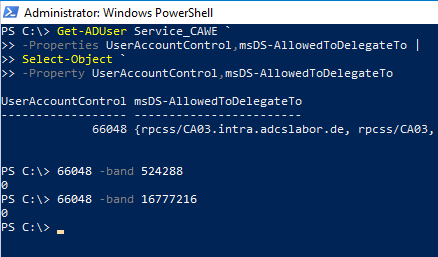
If this option is selected, the target services for delegated authentication can be specified explicitly. Thus, delegated authentication can be explicitly restricted to requesting certificates from a specific certificate authority.
According to current security research, the service portion of msDS-AllowedToDelegateTo is not verified and can be corrupted accordingly if the service account credentials are known to an attacker.
From a security point of view, this option is very good, but there is also the limitation that only the Kerberos protocol can be used.
Details: Trust this user for delegation to specified services only: Use any authentication protocol
Technically, this option is mapped by the fact that the target services are entered in the msDS-AllowedToDelegateTo attribute of the service account and bit 16777216 (TRUSTED_TO_AUTH_FOR_DELEGATION) is set in the UserAccountControl attribute of the service account.
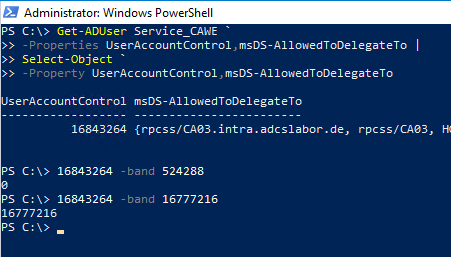
If this option is selected, the target services can be explicitly specified as in the previous option for delegated authentication. In addition, a protocol transition is possible, i.e., a user can authenticate to the web service via NTLM or client certificate, for example, and authentication against the certificate authority can still be done via Kerberos.
However, from a security perspective, this option should be used with caution, as it allows the service account to request tickets for users without the user having to authenticate to the service. Thus, this option should only be used if it can be reasonably ensured that the service account is protected from compromise.
If the service account is a domain account, it is essential to provide it with a strong password and change it regularly. The better choice is to combine it with a Group Managed Service Account (gMSA).
Related links:
- Overview of possible delegation settings for certification authority web registration (CAWE)
- Overview of the possible delegation settings for the Certificate Enrollment Web Service (CES)
3 thoughts on “Grundlagen und Risikobetrachtung Delegierungseinstellungen”
Comments are closed.