All applications that use the Microsoft Cryptographic Application Programming Interface Version 2 (Crypto API Version 2, CAPI2) have a mechanism for caching certificate revocation information (Certificate revocation lists and OCSP-answers).
Thus, there is no guarantee that, for example, a newly published blacklist will be used by participants before the previous blacklist, which is still in the cache, has expired.
The following describes how to view and influence the blacklist cache.
Sometimes it is necessary for a certificate issued by a certification authority to be withdrawn from circulation even before its expiration date. To make this possible, a certification authority keeps a revocation list. This is a signed file with a relatively short expiration date, which is used in combination with the certificate to check its validity.
The Online Responder (Online Certificate Status Protocol, OCSP) is an alternative way of providing revocation status information for certificates. Entities that want to check the revocation status of a certificate do not have to download the complete list of all revoked certificates thanks to OCSP, but can make a specific request for the certificate in question to the online responder. For a more detailed description, see the article "Basics Online Responder (Online Certificate Status Protocol, OCSP)„.
Implementation
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The cache is implemented in two ways:
- Application specific cache
- File system cache
The application-specific cache can only be cleared by exiting and restarting the respective application, since it is kept in memory. For system services, it may therefore even be necessary to restart the computer.
However, the file system cache can be viewed and influenced. You can view the file system cache with the following command.
certutil -urlcache
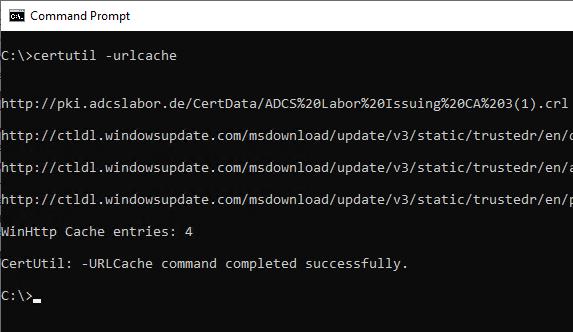
Here, a separation between blacklists and OCSP responses can be made with the following options.
certutil -urlcache crl
certutil -urlcache ocsp
The file system cache can be deleted with the following command:
certutil -urlcache * delete
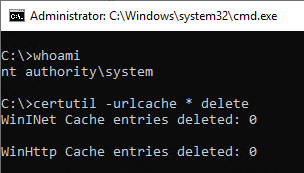
The file system cache exists once per user profile. However, the computer itself with the SYSTEM account is also a user. A deletion of this cache can be done e.g. by a system shell opened with psexec.
For example, clearing the file system cache for the SYSTEM account can be done by running a command line in this security context with a tool such as psexec starts.
psexec -s -i cmd.exe
certutil -urlcache * delete
7 thoughts on “Den Adress-Zwischenspeicher für Sperrlisten (CRL URL Cache) einsehen und löschen”
Comments are closed.