Assume the following scenario:
- A certification authority is implemented in the network.
- The certification authority service does not start.
- When trying to start the Certification Authority service, you get the following error message:
A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT)
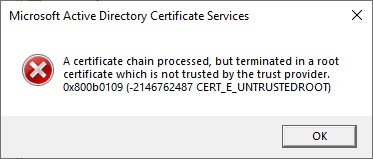
A corresponding Event with no. 100 can also be found in the event display of the certification authority:
Active Directory Certificate Services did not start: Could not load or verify the current CA certificate. ADCS Labor Issuing CA 3 A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT).
Cause
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
This error is closely related to the error CERT_E_CHAINING. In this case, the certificate chain can be formed up to the root certification authority certificate, but this is not located in the trusted root certification authority store on the certification authority.
Solution
In addition to the certification authority itself, all other participants must of course also trust the certificates. It therefore makes sense not only to import the certificates into the local certificate store of the certification authority, but also to distribute them centrally throughout the entire Active Directory structure, e.g. via group policies.
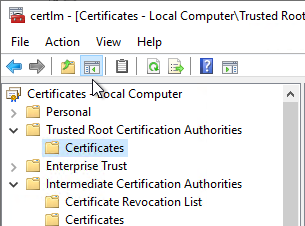
In order to start the certification authority service, the certificate chain, i.e. all certificates up to the root certification authority, must be installed in the computer certificate store of the certification authority computer. This can be done via the certificate management console for the local computer account (certlm.msc).
- Root Certification Authority certificates must be stored in the Trusted Root Certification Authorities certificate store of the computer account.
Related links:
- The certification authority service does not start and throws the error message "A certificate chain could not be built to a trusted root authority. 0x800b010a (-2146762486 CERT_E_CHAINING)".
- The certificate authority service does not start and throws the error message "0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)".
- The certification authority service does not start and throws the error message "The certificate is revoked. 0x80092010 (-2146885616 CRYPT_E_REVOKED)".
- What impact does a non-functioning revocation list of a certification authority certificate have on the certification authority?
- What impact does the revocation of a certification authority certificate have on the certification authority?
- What impact does the revocation of the trust status of a root certification authority certificate have on the certification authority
10 thoughts on “Der Zertifizierungsstellen-Dienst startet nicht und wirft die Fehlermeldung „A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. 0x800b0109 (-2146762487 CERT_E_UNTRUSTEDROOT)“”
Comments are closed.