The following describes how to install the Certificate Enrollment Policy Web Service (CEP).
The Certificate Enrollment Web Services (Certificate Enrollment Policy Web Service, CEP, and Certificate Enrollment Web Service, CES) enable the automatic request and renewal of certificates from a certification authority via a Web-based interface. This eliminates the need to contact the certification authority directly via Remote Procedure Call (RPC). For a more detailed description, see the article "Certificate request basics via Certificate Enrollment Web Services (CEP, CES)„.
The following instructions initially install the roller with the default settings. An adjustment is made in the respective course of the instructions.
Required permissions
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
To install the role, it is required that the installing user is a member of the Enterprise Administrators group. Unfortunately, the permission cannot be delegated. For this reason, special care should be taken when using the user account to prevent identity theft.
Authentication methods supported by CEP
The following combinations of authentication methods are possible. These can all be installed together on the same server.
- Kerberos authentication
- Username/Password Authentication
- Username/password authentication with support for key-based renewal
- Certificate-based authentication
- Certificate-based authentication with support for key-based renewal
Install role files and dependencies
First, the web server role is installed. This step is not strictly necessary, since it is done as a dependency anyway. However, it can be used to ensure that the subsequently required IIS management tools are installed. If there is no Internet Information Service (IIS) Web Server installed on the target server, it can be installed with the default settings and management tools using the following command.
Install-WindowsFeature -Name Web-Server -IncludeManagementTools
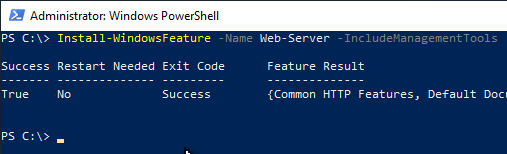
Then the binaries for the CEP can be installed.
Install-WindowsFeature -Name ADCS-Enroll-Web-Pol
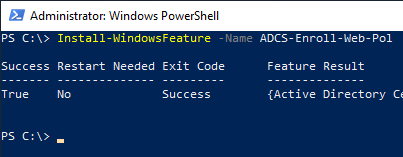
Request SSL certificate
Since the Certificate Enrollment Web Policy Service works over HTTPS, an SSL certificate is required. How to configure a certificate template for such a certificate is described in the article "Configuring a Secure Socket Layer (SSL) Certificate Template for Web Server" described.
The identity within the SSL certificate must match either the fully qualified server name, or the alias should the CEP be operated with one.
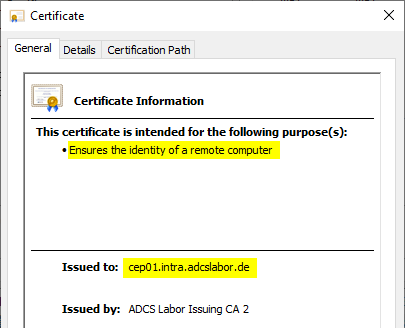
Identify SSL certificate
When installing the CEP role, the SSL certificate just requested must be specified. It can first be identified with the following Powershell command.
Get-ChildItem -Path Cert:\LocalMachine\My
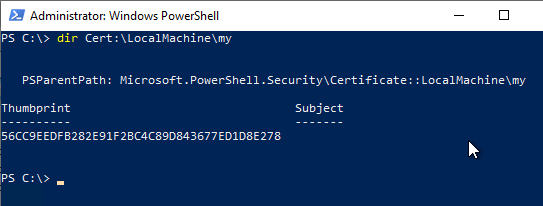
If there are several certificates to choose from, it may help to identify the fingerprint (thumprint) of the certificate via the certificate dialog, for example via the certificate management console for the computer account (certlm.msc).
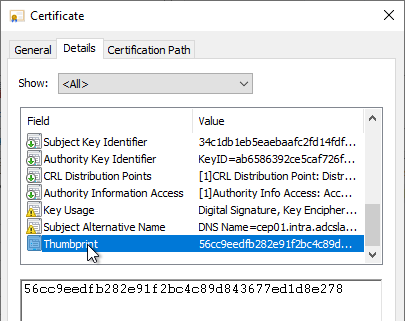
Subsequently, the identified certificate is stored in a variable (here: $sslcert) cached.
$sslcert = dir Cert:\LocalMachine\My\{thumbprint-of-the-certificate}
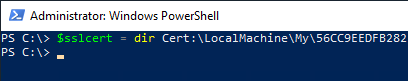
Now this variable can be used to install the individual CEP roles.
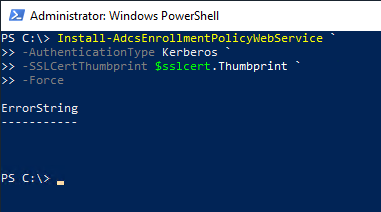
Installation of CEP roles: Kerberos authentication
The following Powershell command can be used to install this role:
Install-AdcsEnrollmentPolicyWebService -AuthenticationType Kerberos -SSLCertThumbprint $sslcert.Thumbprint -Force
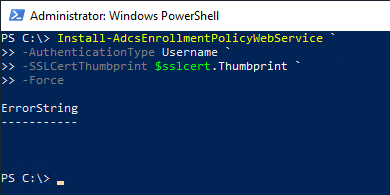
Installation of the CEP roles: Username/Password Authentication
The following Powershell command can be used to install this role:
Install-AdcsEnrollmentPolicyWebService -AuthenticationType Username -SSLCertThumbprint $sslcert.Thumbprint -Force
Installation of CEP roles: Username/Password Authentication with Key-based Renewal Support
The following Powershell command can be used to install this role:
Install-AdcsEnrollmentPolicyWebService -AuthenticationType Username -KeyBasedRenewal -SSLCertThumbprint $sslcert.Thumbprint -Force
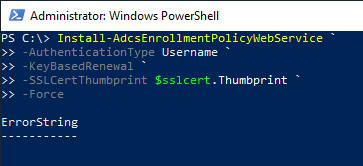
Installation of the CEP roles: Certificate-based authentication
The following Powershell command can be used to install this role:
Install-AdcsEnrollmentPolicyWebService -AuthenticationType Certificate -SSLCertThumbprint $sslcert.Thumbprint -Force
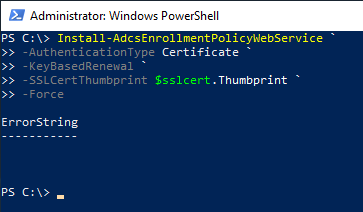
Installation of CEP roles: Certificate-based authentication with support for key-based renewal
The following Powershell command can be used to install this role:
Install-AdcsEnrollmentPolicyWebService -AuthenticationType Certificate -KeyBasedRenewal -SSLCertThumbprint $sslcert.Thumbprint -Force
Closure and rework
The individual CEP roles should now show up in the Internet Information Services (IIS) Manager within the Default Web Site.
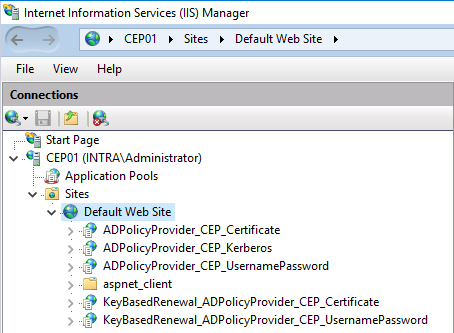
Afterwards, some finishing work may still need to be done:
- Configure alias
- Customize the identity of the IIS application pool
- Installing a Certificate Enrollment Web Service (CES)
- Configuration of a Certificate Request Policy (Enrollment Policy)
Configure alias
If an alias is used for the CEP, it must now be configured. How this is done is described in the article "Configure the Certificate Enrollment Policy Web Service (CEP) for use with an alias." described.
Customize the identity of the IIS application pool
The above commands install the CEP role using the IIS application pool identity.
If this is not desired, the identity of the IIS application pool must now still be changed. How this is done is described in the following two articles:
- Configure the Certificate Enrollment Policy Web Service (CEP) for use with a Group Managed Service Account (gMSA).
- Configure the Certificate Enrollment Policy Web Service (CEP) for use with a domain account.
Installing a Certificate Enrollment Web Service (CES)
A CEP can only be used meaningfully if there is an associated Certificate Enrollment web service (CES) to which certificate requests can be sent. The installation of a CES is described in the article "Installing a Certificate Enrollment Web Service (CES)" described.
Perform function test
Before the CEP can be put into operation, a function test should be performed. The procedure is described in the article "Performing a functional test for the Certificate Enrollment Policy Web Service (CEP)" described.
Configuration of a Certificate Request Policy (Enrollment Policy)
In order to use the certificate request web services, a certificate request policy (enrollment policy) must be defined for the subscribers. The procedure is described in the article "Configuration of a certificate request policy (enrollment policy) for the certificate request web services (CEP, CES)" described.
Related links:
- Configuring a Secure Socket Layer (SSL) Certificate Template for Web Server
- Role configuration for Certificate Enrollment Policy Web Service fails with error message "Access is denied. 0x80070005 (WIN32: 5 ERROR_ACCESS_DENIED)".
- Role configuration for Certificate Enrollment Policy Web Service fails with error message "The argument is null or empty."
- Configure the Certificate Enrollment Policy Web Service (CEP) for use with an alias.
- Configure the Certificate Enrollment Policy Web Service (CEP) for use with a Group Managed Service Account (gMSA).
- Configure the Certificate Enrollment Policy Web Service (CEP) for use with a domain account.
- Certificate request basics via Certificate Enrollment Web Services (CEP, CES)
8 thoughts on “Installation eines Certificate Enrollment Policy Web Service (CEP)”
Comments are closed.