Nowadays, it is essential to protect the authentication of devices on the company network and administrative interfaces. As a rule, digital certificates are used for this purpose.
Printers therefore also generally require digital certificates in order to be operated securely. From a certain number of devices, there is no getting around automatic certificate distribution.
Some printer manufacturers offer centralized management solutions for certificate distribution.
Unfortunately, it has been shown time and again that the secure handling of digital certificates requires a great deal of knowledge, experience and care, which is often not the case.
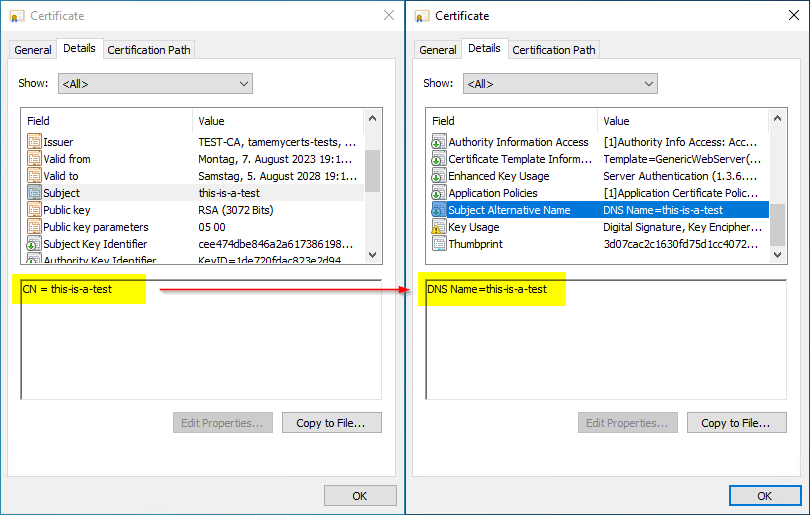
In this specific case, the certificate application is implemented by the management solution in such a way that the mandatory for web server certificates Alternative applicant name not - as it is actually intended - as part of the of the certificate request is transferredbut (Microsoft-proprietary) via the "san" request attribute.
However, this attribute is only processed if the highly dangerous EDITF_ATTRIBUTESUBJECTALTNAME2 flag is activated on the certification authority, which in the worst case can lead to the entire Active Directory structure of the company being compromised.
Here we run into a fairly typical problem in the PKI world: on the one hand, we want to be able to equip all our devices with certificates in order to raise the level of security. On the other hand, we don't want to reduce the security of our PKI to achieve this.
As a rule, you cannot rely on the manufacturer correcting its faulty implementation. It is usually argued that everything works as it should - in this case, the issuing of certificates. Even a supposedly simple change to a software product is often a complicated undertaking for the manufacturer, as the original developer of the code may no longer be available.
So how do we solve the dilemma?
The solution: The TameMyCerts Policy Module for Microsoft Active Directory Certificate Services
With the TameMyCerts Policy Module for Microsoft Active Directory Certificate Services, there is now a way to securely and fully automatically correct incorrect or incomplete certificate requests - without having to activate insecure settings on the certification authority.
TameMyCerts is a Policy moduleto secure the Microsoft certification authority (Active Directory Certificate Services). It extends the functions of the certification authority and enables the Extended application of regulationsto enable the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
So the solution to our dilemma is to disable the dangerous EDITF_ATTRIBUTESUBJECTALTNAME2 on the certificate authority, and configure TameMyCerts to automatically generate the Subject Alternative Name (SAN) from the DNS name present in the Subject Distinguished Name (DN).
TameMyCerts is open source and can be used free of charge. For use in the corporate sector, however, we recommend the Conclusion of a maintenance contract. This ensures that you receive qualified support and that the module can be further developed to a high quality in the long term.
Related links:
- A policy module to tame them all: Introducing the TameMyCerts Policy Module for the Microsoft Certification Authority.
- Active Directory forest compromised by EDITF_ATTRIBUTESUBJECTALTNAME2 flag
- How the TameMyCerts Policy Module for Active Directory Certificate Services (ADCS) can repair incoming certificate requests to make them RFC compliant
- Change the Subject Alternative Name (SAN) of a certificate before it is issued - but do it securely!