Companies use Mobile Device Management (MDM) Products for managing, configuring and updating mobile devices such as smartphones, tablet computers or desktop systems via the Internet (over-the-air, OTA).
Common mobile device management products are:
- Microsoft Intune
- VMware Workspace One (previously known under the brand name AirWatch)
- Ivanti MobileIron UEM
- Jamf Pro
- Baramundi Enterprise Mobility Management
- BlackBerry Enterprise Mobility Suite
- Sophos Mobile Control
- SOTI MobiControl
- Samsung Knox
TameMyCerts is a Policy moduleto secure the Microsoft certification authority (Active Directory Certificate Services). It extends the functions of the certification authority and enables the Extended application of regulationsto enable the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
TameMyCerts is open source and can be used free of charge. For use in the corporate sector, however, we recommend the Conclusion of a maintenance contract. This ensures that you receive qualified support and that the module can be further developed to a high quality in the long term.
Functionality
All of these systems use a similar concept in conjunction with a Microsoft certification authority: they act as a middleman between the managed device, the company's directory service and the certification authority. In PKI terms, they perform the role of the Registration Authority (RA) from. They all use a type of connector to transfer certificate requests to the Microsoft AD CS certification authority.
All common MDM systems therefore require that the configured certificate template is set up as an offline certificate template, i.e. that the identity contained in the certificate and confirmed by the certification authority is specified by the applicant, i.e. the MDM system ("enrollee supplies subject").
The certification authority has therefore no knowledge of the requested certificate contentit issues the certificate requests blindly and must trust the MDM system completely.
Misplacements by the MDM system are not uncommon
Unfortunately, it is not uncommon for incorrect settings to be made by the MDM system or with its authorizations. Possible reasons could be
- Misconfiguration of the MDM system.
- Misbehavior of the MDM system. For example, certificates may be requested for devices that are no longer assigned to an existing user. In this case, certificates with empty identities may be requested.
- Compromising the service account used and exploiting its application authorizations (see ESC1 attack).
This opens the door to security and data protection incidents.
The usual installations of MDM systems in conjunction with Microsoft Active Directory Certificate Services are therefore vulnerable to the Swiss cheese modelin which small gaps running through the chain of all systems involved can lead to major damage.
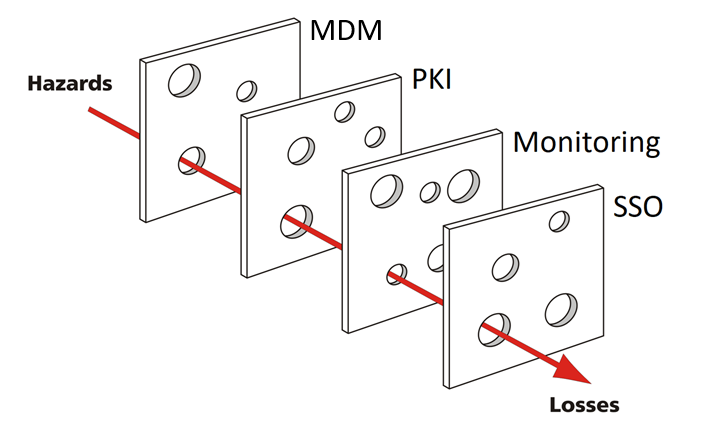
Specific example: No valid user is assigned to a managed device
In practice, it often happens with MDM systems that no valid user account is assigned to a managed end device.
In a simple case, for example, it would be configured that the Subject Distinguished Name (DN) of a certificate contains a commonName with the variable of the user name.
CN={EnrollmentUser}
In this example, the syntax of VMware Workspace One is used, but all common MDM systems work in a similar way.
If this variable is now empty because no valid user account is assigned to the end device, a certificate request with an empty Subject Distinguished Name (DN) may be generated. MDM systems obviously behave differently here:
- Baramundi Enterprise Mobility Management generates an empty sequence in this case and the certification authority will reject the certificate request with the error message "Error Parsing Request The request subject name is invalid or too long. 0x80094001 (-2146877439 CERTSRV_E_BAD_REQUESTSUBJECT)" reject.
- VMware Workspace One will generate a certificate request with a Subject Distinguished Name (DN), which contains an empty commonName. Such a certificate request is issued by the certification authority. However, the resulting certificate will not contain an identity.
If the application that checks the certificate at logon (e.g. a single sign-on (SSO) system) is unlucky enough to be unable to handle such a case adequately, it may happen that the identity of another valid user is assigned with such a certificate at logon. The data protection and security incident is complete.
The solution: TameMyCerts
The TameMyCerts Policy Module for Microsoft Active Directory Certificate Services can close the gap at the certificate authority level by controlling certificate requests by enforcing a fine-grained set of rules.
The possibilities include, among others:
- Enforcing syntax rules for the requested Subject Distinguished Name and Subject Alternative Name.
- Creating a Connection between the requested identity in the certificate and the corresponding object in the Active Directory. Applying rules against the associated object, e.g. based on the status (active or deactivated), membership in groups or organizational units and other criteria.
- Modify the requested certificate content before the certificate is issued. Transfer or remove certificate fields, add static values or values from the associated Active Directory object.
Certificate requests that violate the defined rules will be rejected and the incident logged. This means that an alarm can also be set up to follow up potential security incidents.
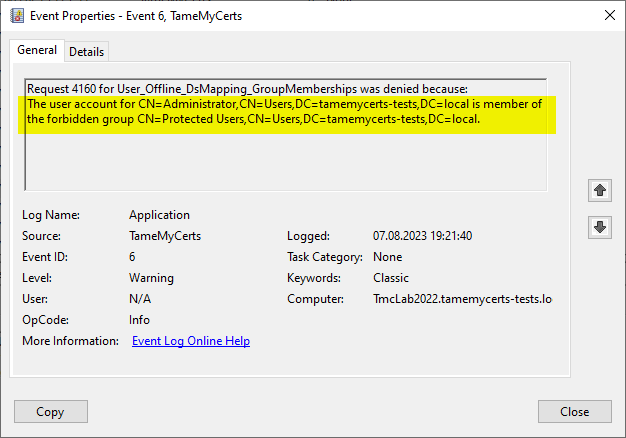
Microsoft Intune uses the Network Device Enrollment Service (NDES) as a connector between Intune and the certification authority. NDES, as well as the certification authority itself, can be extended with policy modules. Microsoft provides a policy module for NDES for Intune, so no further policy module can be added to an NDES instance that has been configured for Intune. However, since TameMyCerts operates at the level of the certification authority and is installed on it, the advantages of both modules can be easily combined.
Related links:
- A policy module to tame them all: Introducing the TameMyCerts Policy Module for the Microsoft Certification Authority.
- Network Device Enrollment Service (NDES) Basics