With the supposedly good intention of making it possible to issue such certificate requirements with a SAN, guess unfortunately much at many Instructions to set the flag on the certification authority EDITF_ATTRIBUTESUBJECTALTNAME2 to activate.
If this flag is activated, a very large attack surface is offered, as any applicant can now instruct the certification authority to issue certificates with any content. This type of attack is known in the security scene as ESC6 and ESC7 known.
TameMyCerts is a Policy moduleto secure the Microsoft certification authority (Active Directory Certificate Services). It extends the functions of the certification authority and enables the Extended application of regulationsto enable the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem and is available under a free license. It can downloaded via GitHub and can be used free of charge.
TameMyCerts is open source and can be used free of charge. For use in the corporate sector, however, we recommend the Conclusion of a maintenance contract. This ensures that you receive qualified support and that the module can be further developed to a high quality in the long term.
ESC6 and ESC7 utilize certification bodies that use the EDITF_ATTRIBUTESUBJECTALTNAME2 flag globally. If this flag is activated in the configuration of a certification authority - whether intentionally or by mistake an attacker can send a request attribute with malicious content to the certification authority, while submitting a certificate request. The certification authority is then instructed to enter the content of the submitted attribute in the Subject Alternative Name (SAN) of the issued certificate, regardless of what was configured in the certificate template.
TameMyCerts ensures that such attempts to exploit the certification authority are recognized and prevented if the flag from the certification authority is activated. The rejected certificate request is is loggedso that an alarm can be raised and further measures taken.
The fact that TameMyCerts can recognize malicious application attributes and log corresponding attempts is the core of the Certiception Honeypot Toolkit for Active Directory Certificate Services and thus allows attackers to be unmasked at an early stage.
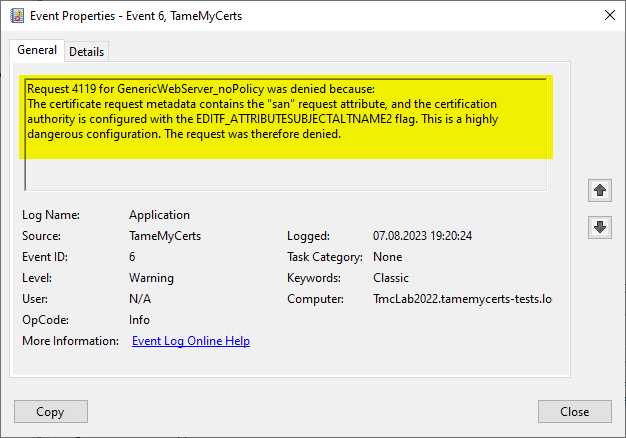
Administrators sometimes activate this flag with the intention of attaching SAN certificate extensions to certificate requests that do not include it, for example because the application or appliance used cannot create certificate requests with SAN. In most cases, these are web server certificates that require a SAN extension for modern browsers to accept the connection. To solve this problem, TameMyCerts has developed a corresponding function to securely and automatically transfer recognized DNS names and IP addresses from the Subject Distiguished Name to a newly created SAN extension.
Related links:
- A policy module to tame them all: Introducing the TameMyCerts Policy Module for the Microsoft Certification Authority.
- How the TameMyCerts Policy Module for Active Directory Certificate Services (ADCS) can repair incoming certificate requests to make them RFC compliant
- Active Directory forest compromised by EDITF_ATTRIBUTESUBJECTALTNAME2 flag
- Change the Subject Alternative Name (SAN) of a certificate before it is issued - but do it securely!