Assume the following scenario:
- A Certification Authority uses a Hardware Security Module (HSM).
- The partition of the hardware security module fills up with more and more keys over the lifetime of the certificate authority.
- At SafeNet hardware security modules, this can even cause the partition to fill up. As a result, the events 86 and 88 logged by the Certification Authority.
This phenomenon can generally occur with all hardware security modules used, but is most likely to cause visible problems with SafeNet Luna HSMs, where there is only limited storage space available for keys per partition.
Cause and background
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The Microsoft Certification Authority regularly generates new certificates for Certificate Authority Exchange ("CA Exchange") (from the eponymous Certificate Template), which also does not have to be explicitly published on a certification authority.
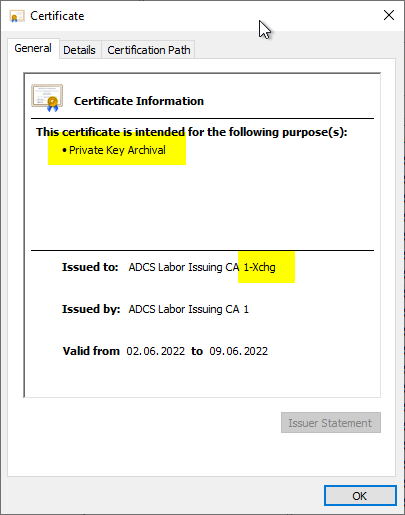
As you can see, the "CA Exchange" certificates use the Extended Key Usage for "Private Key Arrchival". This should - when restricting the extended key usages of a certification authority - must always be included in the list of allowed extended key usages for the certification authority certificate, since otherwise no certificates can be generated for the certification authority exchange.
The "CA Exchange" certificates are used by the certification authority for the following purposes:
- Will the Private key archiving is used, a client can use the public key of this certificate to securely transmit the private key to be archived to the certification authority.
- The Enterprise PKI Management Console (pkiview.msc) uses the contents of the "CA Exchange" certificate to determine the CRL Distribution Points (CDP) and Authority Information Access (AIA) and display their status in the overview.
The RPC/DCOM interface of the Certification Authority offers the ICertRequest::GetCaCertificate method, which can be used by all users in the network (Authenticated Users) to retrieve the "CA Exchange" certificate.
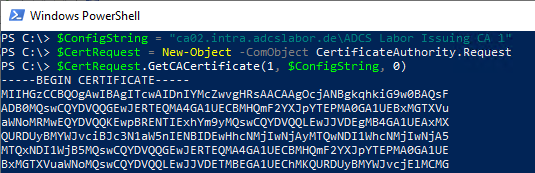
A corresponding query can also be made very easily with Windows PowerShell:
$ConfigString = "{hostname-of-the-CA}\{common-name-of-the-CA}"
$CertRequest = New-Object -ComObject CertificateAuthority.Request
$CertRequest.GetCACertificate(1, $ConfigString, 0)
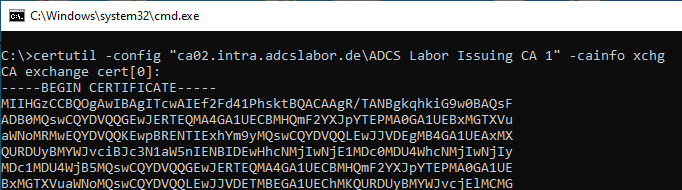
Alternatively, the query can be done via certutil:
certutil -config "{hostname-of-the-CA>\{common-name-of-the-CA>" -cainfo xchg
Certificates for certification authority exchange have a relatively short validity period of only one week, so that the keys are renewed regularly.
When installing a certification authority, the Key Storage Providerwhich is used for the certification authority certificate, is also adopted 1:1 for the certification authority exchange certificate.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\{Common-name-of-CA}\EncryptionCSP
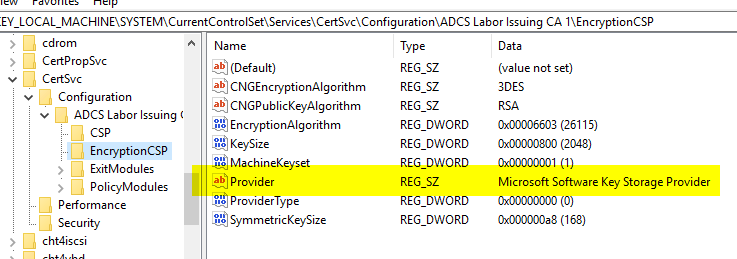
Evaluation
Even though confidential information tends to be transmitted with this type of certificate, the weekly change of the certificate and thus also of the private key ensures security even without a hardware security module. The keys are also only used to transmit the data, not to store it. Switching to a software provider is therefore not dangerous and also makes sense.
Implementation
To switch back to a software provider for the certification authority exchange certificates, it is sufficient to run the following command line command on the certification authority:
certutil -setreg CA\EncryptionCSP\Provider "Microsoft Software Key Storage Provider".
Afterwards, the certification authority service must be restarted for the changes to take effect.
When restarting the certification authority, please take into account that there is a known error with the SafeNet Key Storage Provider, which can lead to the following when restarting the service Error code RPC_S_DUPLICATE_ENDPOINT can result. Allow sufficient waiting time between stopping and starting the service.
Related links:
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
- Basics: Cryptographic Service Provider (CSP) and Key Storage Provider (KSP)
- Basics: Restricting Extended Key Usage (EKU) in Certification Authority Certificates
2 thoughts on “Die Partition des Hardware Security Moduls (HSM) läuft voll”
Comments are closed.