In a networked world, it has become standard to work from anywhere, and also to work with mobile end devices such as smartphones or tablets in addition to classic desktop computers. Such end devices are usually connected by means of Mobile Device Management (MDM) managed by systems such as Microsoft Intune.
In most cases, users of mobile devices need digital certificates to prove their identity in order to gain access to corporate resources. Thus, it is necessary to provide these devices with an automatable yet secure interface for applying for these certificates.
The certificate application for end devices managed with Microsoft Intune faces the challenge that the devices are not connected to the corporate network like classic office computers, but are usually managed over the air (OTA).
Similarly, the devices (unlike their users) do not have an account in the Active Directory directory service.
Microsoft has therefore decided to map the certificate application for end devices managed with Intune via the Network Device Enrollment Service (NDES).
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Functionality
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
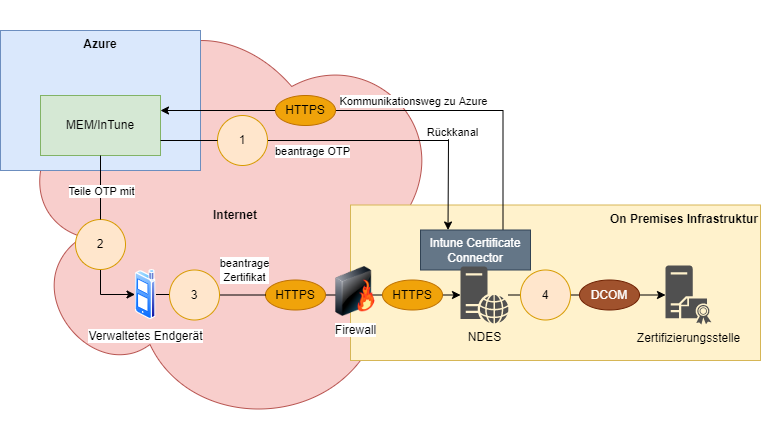
The Intune Certificate Connector is installed on the NDES server. This brings a policy module for NDES, so that this NDES server can no longer be used apart from Intune.
- Intune requests a one-time password (OTP) from the NDES server for the managed device in question.
- The one-time password is transmitted to the managed terminal device. The public address of the NDES server is also communicated to the end device in this process.
- The managed terminal now creates a certificate request and now applies for a certificate for the user via the Internet from the NDES server using the OTP it has received.
- The NDES server forwards the certificate request via DCOM protocol to the certification authority.
As you can see from the procedure and the corresponding documentation, the NDES server must be accessible from the Internet:
To allow devices on the internet to get certificates, you must publish your NDES URL external to your corporate network. To do this, you can use a reverse proxy like Azure AD Application Proxy, Microsoft's Web Application Proxy Server, or a third-party reverse proxy service or device.
Configure infrastructure to support SCEP with Intune (Microsoft Corporation)
Related links:
- Basics of manual and automatic Certificate Enrollment via Lightweight Directory Access Protocol (LDAP) and Remote Procedure Call / Distributed Common Object Model (RPC/DCOM)
- Network Device Enrollment Service (NDES) Basics
External sources
- Certificate Connector for Microsoft Intune (Microsoft Corporation)
- Configure infrastructure to support SCEP with Intune (Microsoft Corporation)