If the Network Device Enrollment Service (NDES) is reinstalled (Preferably without Enterprise Administrator permissions), only the Windows-integrated authentication for the administration web page is activated at first. With this (via NT LAN Manager, NTLM) protocol, authentication via user name and password is also possible. However, not all client applications support this.
Likewise, a company might be willing to, Disable NTLM where possible and enforce Kerberos for login. Enforcing Kerberos removes the ability to log in to the Network Device Registration Service administration page via username and password (since this is done with NTLM credentials). However, Basic Authentication can be retrofitted to provide an option here again.
One way out of this dilemma can be Basic Authentication, the setup of which will be explained below.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
It should be absolutely ensured that the administration web page is configured to use SSL and this is enforced. For the application web page, on the other hand, this is not required.
First, Basic Authentication must be added to the Internet Information Service (IIS) features.
Add-WindowsFeature -Name Web-Basic-Auth
After the web server service is restarted, the IIS Manegement Console is launched and the "View Applications" option is called in the Default Web Site on the right side.
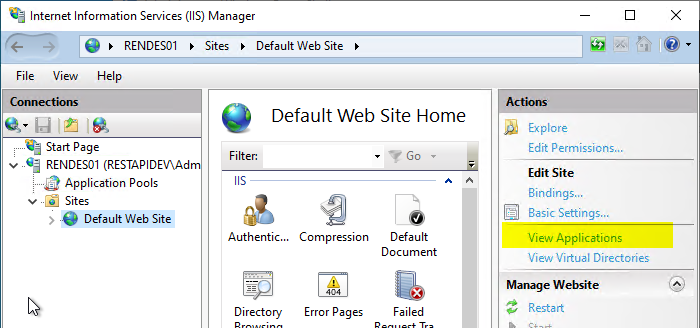
Double-click to open the settings for "/certsrv/mscep_admin".
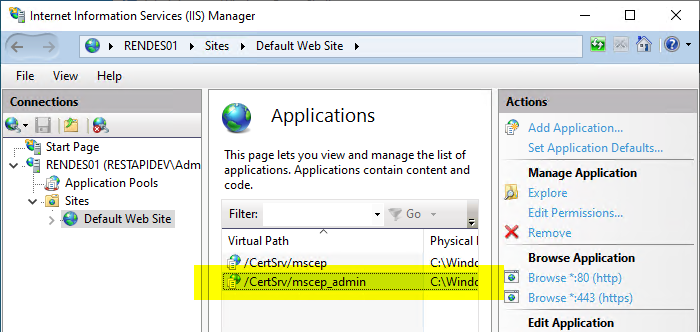
Here you select the option "Authentication".
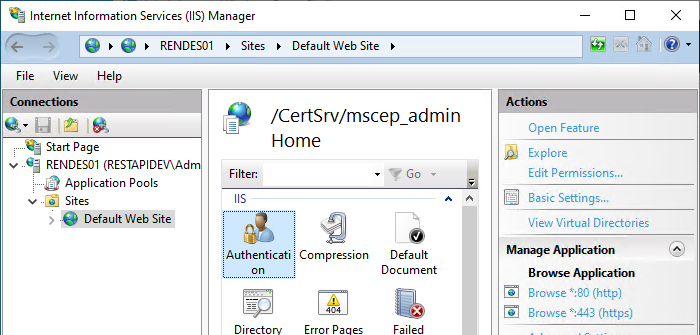
The "Basic Authentication" option is activated.
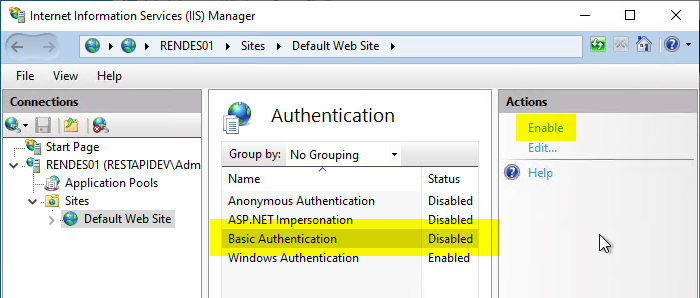
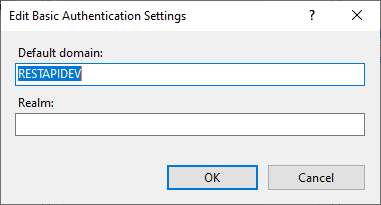
Then click on the "Edit" button and enter a default domain in the following dialog.
Function test
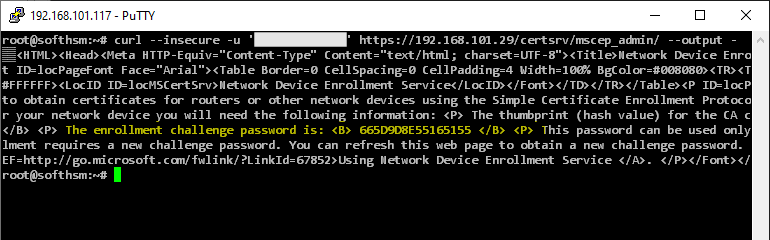
For testing purposes the tool curl which is included in practically every Linux distribution. A Windows version also exists.
curl -u 'username:Password' https://{NDES-Server}/certsrv/mscep_admin/ --output -
The command line arguments mean the following:
- "-output -" forces the output to the command line, since NDES uses UTF16-LE encoding, which is recognized as "binary" by curl
- "-insecure" optionally skips the server certificate check (Not recommended for productive use)
One thought on “Aktivieren der Basic Authentication für den Registrierungsdienst für Netzwerkgeräte (NDES)”
Comments are closed.