In the default configuration, the Network Device Enrollment Service (NDES) only accepts unencrypted connections via HTTP. It is recommended that at least the NDES administration web page be configured for HTTP over TLS (HTTPS) to make it difficult to capture network traffic. The following is a guide.
For a closer look at the need to use SSL, see the article "Should HTTPS be used for the Network Device Enrollment Service (NDES)?„.
The Network Device Enrollment Service (NDES) provides a way for devices that do not have an identifier in Active Directory (for example, network devices such as routers, switches, printers, thin clients, or smartphones and tablets) to request certificates from a certification authority. For a more detailed description, see the article "Network Device Enrollment Service (NDES) Basics„.
Apply for an SSL certificate
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
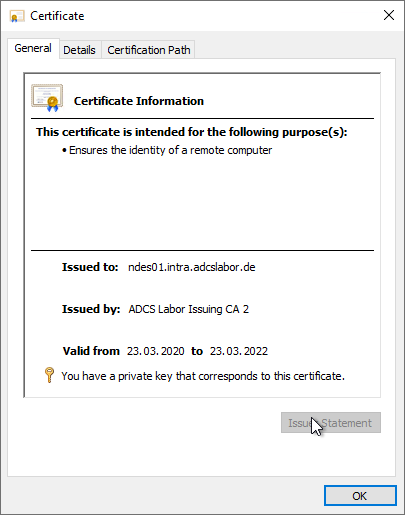
First, a Web Server certificate must be requested for the NDES server.
- In the article "Configuring a Secure Socket Layer (SSL) Certificate Template for Web Server" describes how to create a certificate template for SSL.
- In the article "Generating a RFC 2818 compliant certificate request for SSL certificates" describes how to create an RFC2818 compliant certificate request for SSL certificates.
Binding the SSL certificate to the NDES server
After an SSL certificate has been requested for the NDES server, it must now be bound to the web server. To do this, the Internet Information Services (IIS) Manager is called up via the administration tools.
NDES is installed in the default web site of the web server. Accordingly, the bindings must be edited here.
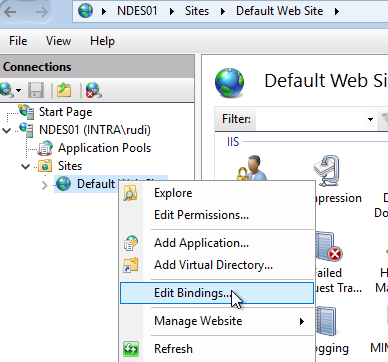
If there is no SSL binding yet, a new one must be created.
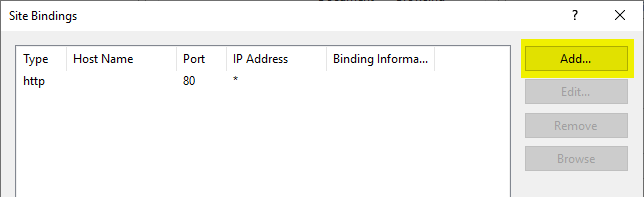
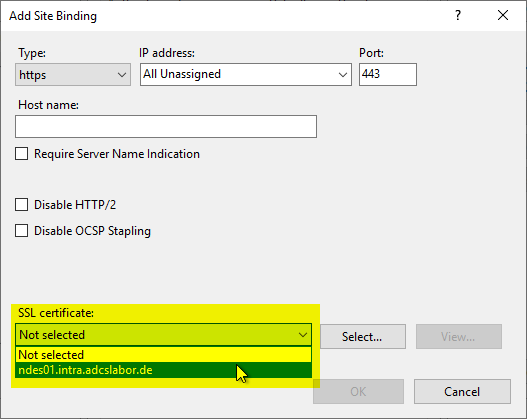
The Default Web Site should answer all requests not defined otherwise, so the default setting regarding IP addresses and hostnames can be kept. Only the SSL certificate must be selected.
Enforce SSL usage
Now the web server supports requests via HTTPS, but for NDES these are not enforced, i.e. requests can still be submitted via HTTP. If you want to enforce SSL specifically for NDES, go to the default web site and click "View Applications" on the right side.
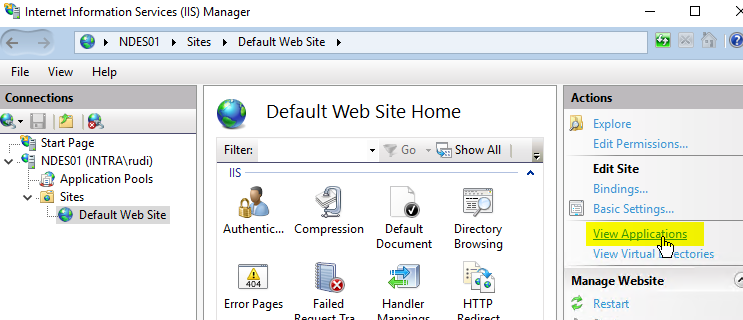
NDES splits into two applications:
- The interface for requesting one-time passwords (mscep_admin)
- The interface for requesting the certificates (mscep)
It is recommended to force HTTPS at least for the mscep_admin application to prevent the logging of credentials. The mscep application can optionally also be configured to force HTTPS, but this is not absolutely necessary since encryption already takes place at the protocol level (see article "Should HTTPS be used for the Network Device Enrollment Service (NDES)?"."). The procedure is identical and is therefore described only once for the mscep_admin application.
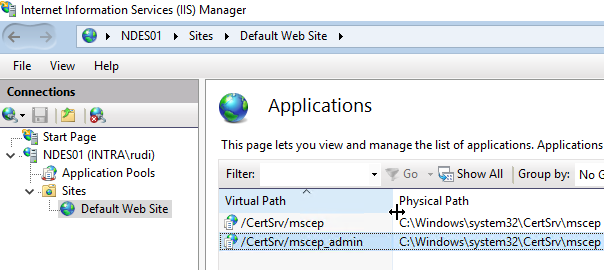
After double-clicking on the application, select the "SSL Settings".
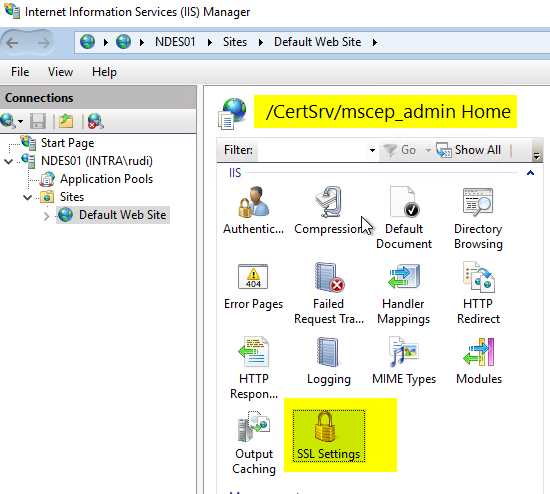
Here you activate the "Require SSL" checkbox.
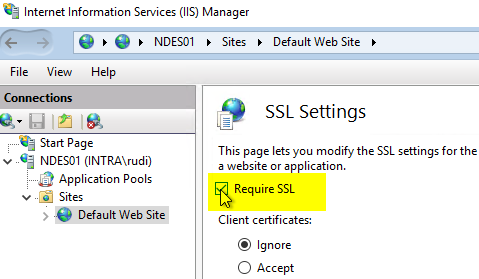
Then click on "Apply" on the right-hand side.
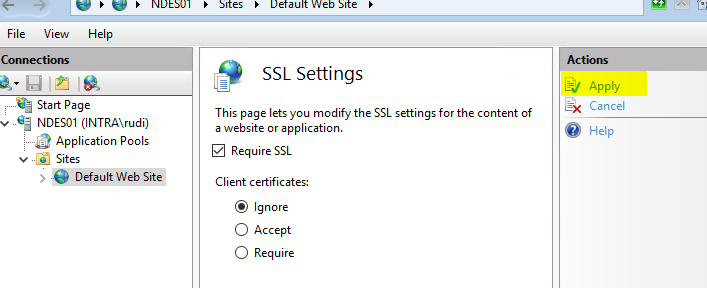
Now, if desired, the mscep can be configured according to the identical pattern. One clicks before once on a node outside of the default web site and afterwards again on the default web site, in order to receive the applications again for the selection.
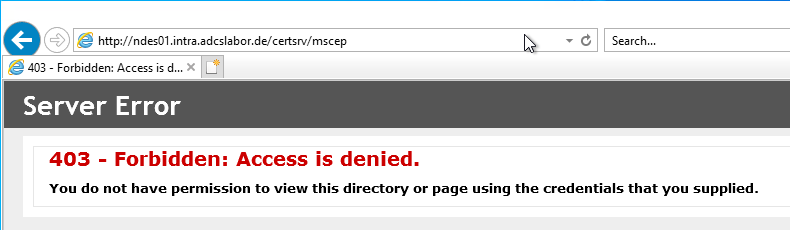
NDES should now refuse to accept connections over HTTP without TLS.
9 thoughts on “Secure Sockets Layer (SSL) für den Registrierungsdienst für Netzwerkgeräte (NDES) aktivieren”
Comments are closed.