Nachfolgend eine Übersicht über die für die Public Key Infrastruktur relevanten vom Remotedesktop-Sitzungshost erzeugten Ereignisse in der Windows-Ereignisanzeige.
Ereignisquellen
Die Ereignisse des Remotedesktop-Sitzungshosts werden in das System-Protokoll geschrieben. Folgende Quellen enthalten PKI-relevante Ereignisse:
- Microsoft-Windows-TerminalServices-RemoteConnectionManager
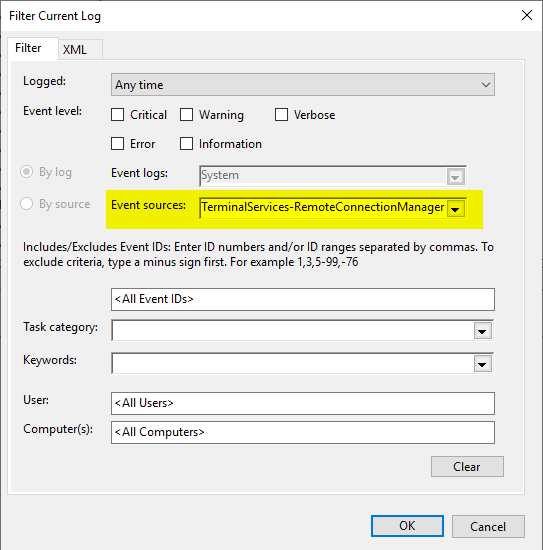
Es empfiehlt sich, einen Filter auf das System-Ereignisprotokoll anzuwenden.
Kennen Sie TameMyCerts? TameMyCerts ist ein Add-On für die Microsoft Zertifizierungsstelle (Active Directory Certificate Services). Es erweitert die Funktion der Zertifizierungsstelle und ermöglicht die Anwendung von Regelwerken, um die sichere Automatisierung von Zertifikat-Ausstellungen zu realisieren. TameMyCerts ist einzigartig im Microsoft-Ökosystem, hat sich bereits in unzähligen Unternehmen auf der ganzen Welt bewährt und steht unter einer freien Lizenz. Es kann über GitHub heruntergeladen und kostenlos verwendet werden. Professionelle Wartung wird ebenfalls angeboten.
Ereignisquelle Microsoft-Windows-TerminalServices-RemoteConnectionManager
Kennen Sie TameMyCerts? TameMyCerts ist ein Add-On für die Microsoft Zertifizierungsstelle (Active Directory Certificate Services). Es erweitert die Funktion der Zertifizierungsstelle und ermöglicht die Anwendung von Regelwerken, um die sichere Automatisierung von Zertifikat-Ausstellungen zu realisieren. TameMyCerts ist einzigartig im Microsoft-Ökosystem, hat sich bereits in unzähligen Unternehmen auf der ganzen Welt bewährt und steht unter einer freien Lizenz. Es kann über GitHub heruntergeladen und kostenlos verwendet werden. Professionelle Wartung wird ebenfalls angeboten.
| ID | Typ | Ereignistext |
|---|---|---|
| 1051 | The RD Session Host Server is configured to use SSL with user selected certificate, however, no usable certificate was found on the server. The default certificate will be used for RD Session Host Server authentication from now on. Please check the security settings by using the Remote Desktop Session Host Configuration tool in the Administrative Tools folder. | |
| 1052 | The RD Session Host Server is configured to use a certificate that will expire in %2 days. %1 The SHA1 hash of the certificate is in the event data. Please check the security settings by using the Remote Desktop Session Host Configuration tool in the Administrative Tools folder. | |
| 1053 | The RD Session Host Server is configured to use a certificate that is expired. %1 The SHA1 hash of the certificate is in the event data. The default certificate will be used for RD Session Host Server authentication from now on. Please check the security settings by using the Remote Desktop Session Host Configuration tool in the Administrative Tools folder. | |
| 1054 | The RD Session Host Server is configured to use a certificate that does not contain an Extended Key Usage attribute of Server Authentication. %1 The SHA1 hash of the certificate is in the event data. The default certificate will be used for RD Session Host Server authentication from now on. Please check the security settings by using the Remote Desktop Session Host Configuration tool in the Administrative Tools folder. | |
| 1055 | The RD Session Host Server is configured to use a certificate but is unable to access the private key associated with this certificate. %1 The SHA1 hash of the certificate is in the event data. The default certificate will be used for RD Session Host Server authentication from now on. Please check the security settings by using the Remote Desktop Session Host Configuration tool in the Administrative Tools folder. | |
| 1056 | Information | A new self signed certificate to be used for RD Session Host Server authentication on SSL connections was generated. The name on this certificate is %1. The SHA1 hash of the certificate is in the event data. |
| 1057 | The RD Session Host Server has failed to create a new self signed certificate to be used for RD Session Host Server authentication on SSL connections. The relevant status code was %1. | |
| 1058 | The RD Session Host Server has failed to replace the expired self signed certificate used for RD Session Host Server authentication on SSL connections. The relevant status code was %1. | |
| 1059 | The RD Session Host Server authentication certificate configuration data was invalid and the service reset it. If the computer was configured to use a specific certificate, please verify it is available in the certificate store and use the administrative tools to select it again. | |
| 1062 | The RD Session Host server is configured to use a template-based certificate for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption, but the subject name on the certificate is invalid. %1 The SHA1 hash of the certificate is in the event data. Therefore, the default certificate will be used by the RD Session Host server for authentication. To resolve this issue, make sure that template used to create this certificate is configured to use DNS name as subject name . | |
| 1063 | Information | A new template-based certificate to be used by the RD Session Host server for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption has been installed. The name for this certificate is %1. The SHA1 hash of the certificate is provided in the event data. |
| 1064 | Fehler | The RD Session Host server cannot install a new template-based certificate to be used for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption. The following error occured: %1. |
| 1065 | The template-based certificate that is being used by the RD Session Host server for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption has expired and cannot be replaced by the RD Session Host server. The following error occurred: %1. | |
| 1072 | The cn column for the template-based certificate %1 returned an unknown data type %2. | |
| 1073 | The msPKI-Cert-Template-OID column for the template-based certificate %1 returned an unknown data type %2. |